Have you ever experienced cold sweat and that feeling of restlessness when you went to get hold of your mobile and could not find it? If it has occurred because we have lost it, or in the worst case because it has been stolen by someone else's friends. And that is a very unpleasant feeling.
Faced with that situation We must not lose our temper, but we must act without delay to take a series of measures that can avoid further headaches and undesirable problems.
Since today mobile phones are the switchboard for our information, and we store abundant private information, photos, documents, bank details, etc., loss or theft is a great disorder. That is why we are going to see some very useful tips to know what to do when our cell phone is stolen. Unfortunately, it is unlikely that we will recover the smartphone, but at least we will try to keep the consequences minimal and not affect us too much.

How to locate a stolen mobile?
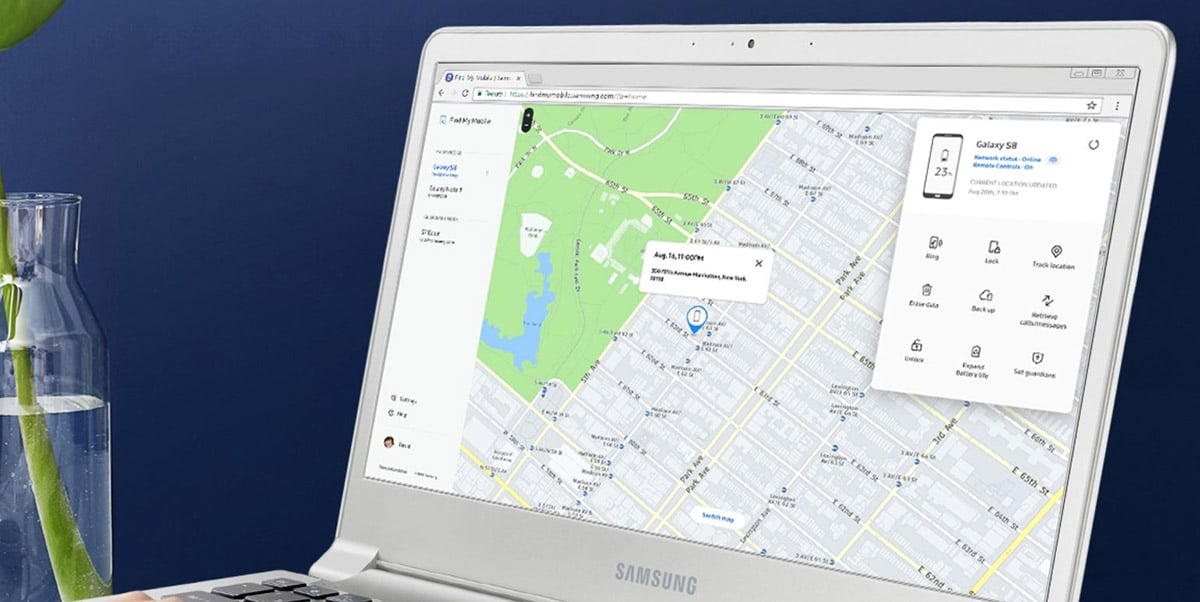
If it is a mobile with Android operating system, thanks to Google We can go to the Android Device Manager page through which we can know the place where the mobile can be found. It also includes among its options the possibility of making the phone ring for 5 minutes even if it was in silent mode, we can block the device or ultimately erase all its content, to avoid greater evils.

If you are a user of the bitten apple, and your mobile was an iPhone, Apple has another tool similar to Google's to find a stolen mobile. In this case it is called "Find my iPhone", if your iOS operating system is version 9 onwards you can perform the search in the same way.
To activate the location and find our iPhone we must go to Settings -> iCloud -> Find my iPhone, And in the event that we have lost it, you can perform the same actions as in Android over the Internet, but thanks to the icloud.com system where we must enter the corresponding data for the Apple ID and the password that we have designated.
Other measures to take in case of theft

Then if the previous steps did not work, we have to call our mobile phone operator to proceed to block the SIM card, since if we have deleted the information it does not mean that they can use your SIM card or send SMS. Therefore, it is best to also block the line as soon as possible, there are operators that allow us to do this from the application or its website with our user. If you don't know how to do it, call the Customer Service phone number or go to the nearest store to have it done for you.
Continuing with the locks, do not forget to do it also through the IMEIThanks to a number that appears on the device box, or that we can find out and keep safely by pressing the code * # 06 # this operation must be carried out before any possible theft occurs, of course. You can also find it on the invoice, on a sticker that they bring on the back, etc.
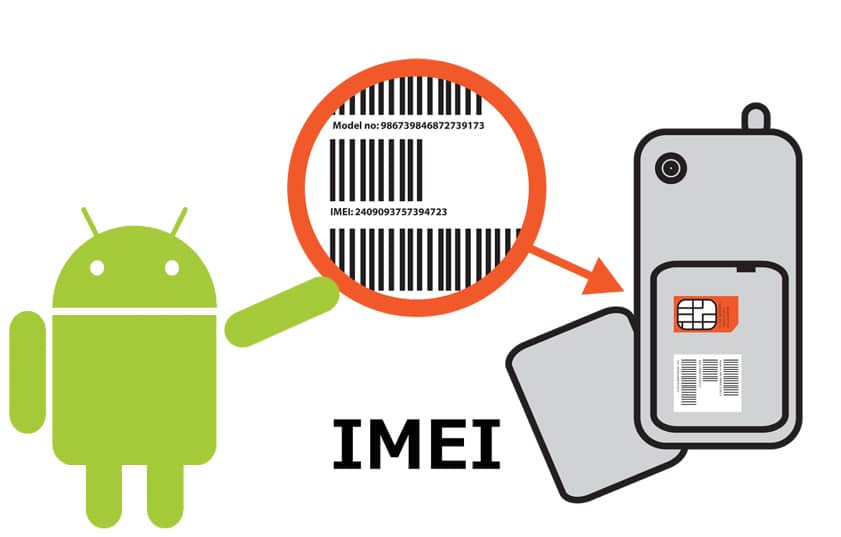
If you still did not write it down or you cannot locate the IMEI, do not worry, there are more ways to know the number, the first thing you should do is enter the Google control page, and you can access it from here . Log in with the Google account that you would have associated with the mobile phone that has been stolen, then click on the "Android" section, and a list of all the mobile phones that you associated with that Gmail account will appear, both the previous and the current one.
On the right side of the mobile models that appear you will be able to read the IMEI number of that particular phone. You can now provide that number to the operator to proceed with locking the phone and thus making it a nice paperweight.
The next thing you should do, if not the first thing, is put the corresponding complaint in the police station to report the theft. We already know that it is difficult to recover it, but depending on the value of the phone it may be a crime, and not a simple theft, therefore it is always advisable to file a complaint. You must provide all the data and especially the IMEI number of the mobile to be able to identify it with total security.
Another action to follow if we want to continue making calls is to request a duplicate SIM card and put it on a new phone. At least this way we have the option to continue using our line for the moment. We can carry out these procedures in the store or by calling our operator, and they will send a new SIM, and although it may cost money, the amount varies according to the criteria of each operator.
Another highly recommended option is to include it in our home insurance as well insured, and with theft coverage. Since in that case the insurance company can manage compensation for the damages caused, and according to the valuation and conditions of the insurance you will be able to compensate some of the damage produced.

If the phone had not been stolen, and it was a loss, we have another option to try to recover it. Consists in configure a message on the lock screen with some information such as our name and an alternative phone number, Either from our partner or a close relative, whom they can call if the person who finds it is honest enough to be able to return it.
Applications to prevent theft
To finish we are going to list and comment on applications that can help you avoid theft and avoid annoyances, for this also remember to have the GPS location activated, because it will be necessary to be able to locate it better, as we have already seen. Therefore, we can resort to third-party applications that can help us in case of theft.
Lookout
The application itself is an antivirus, but Among its functions we have a phone tracking system that can help us a lot. This function can email you the last location of the terminal. And the best thing is that if they turn off the phone and then turn it on again, we will receive a warning at that time and immediately send us the last geolocated position.
Includes the option to take a photo to the person who holds it, send it by mail, Sometimes the photo can be useful either to identify the alleged thief or because it captures a place that is familiar to us or we can identify. It is a function that can help us even if it is not the most precise to recover it.
Prey Anti-Theft
With this application you can protect up to three devices with the same account. Like the previous one allows locate the terminal by geolocation, delete stored data and lock the device. You can also take photos of the friend of others and receive them to identify it and try to recover it more easily.
Anti-theft alarm
This application, like its own idical name, is based on an alarm that deters thieves, or gossips who want to mess with your phone. It makes a loud sound if it is moved, or unplugged from the charger, and it won't stop until you enter the owner-designed key.
Wheres My Droid
This app will offers all the necessary tools for the encryption of information, applications and files on your phone. You can get the GPS location of the phone, set a location alert when the battery always runs out before the phone is turned off, remotely activate the phone's ringer and vibrate.
Through its website you can activate or deactivate any of the options you need, and be able to search for the location of your smartphone. In your hand is to establish the keys you want for the different applications that you have downloaded, configure notifications if the SIM changes and many more options.
Hopefully you never have to use any of these applications, or suffer the theft of your phone, but it is always advisable to be forewarned and have the necessary tools to be able to recover it, or at least try.