
The use of the Bootloader of an operating system is extremely common, but currently not many users know about the Bootloader. So they don't understand the usefulness of using this method on their mobile devices.
In this article we will try to talk to you and explain what Bootloader is and what it is for using it on Android devices.
What is a Bootloader?
This is a bootloader that is present in all operating systems, even those of desktops or mobile devices.
What is a Bootloader for?
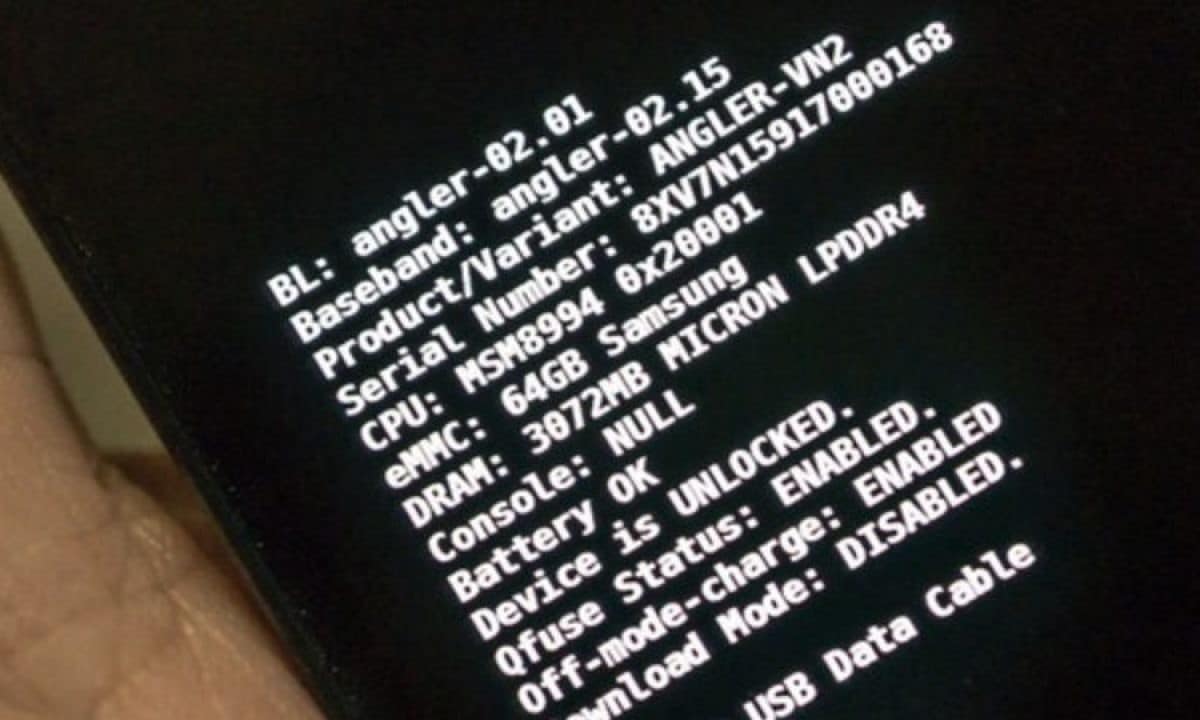
The purpose of a bootloader is be able to perform functional checks before starting the operating system. It is also the one that is in charge of giving the instructions to the operating system so that it can start.
To put it more simply, when you start a mobile or a computer, The first thing that will start is the Bootloader to verify that the components of the operating system are correct and it can start correctly. The first thing it does is check the boot and recovery partitions, after it verifies that everything works, it runs the system kernel and thus finishes the boot.
In the event that something goes wrong, the user will receive an error message explaining why the system has not started. When it already verifies the operating system, it serves as a guide for it to take the steps it must take to complete the startup process.
What state is the bootloader in on mobiles?
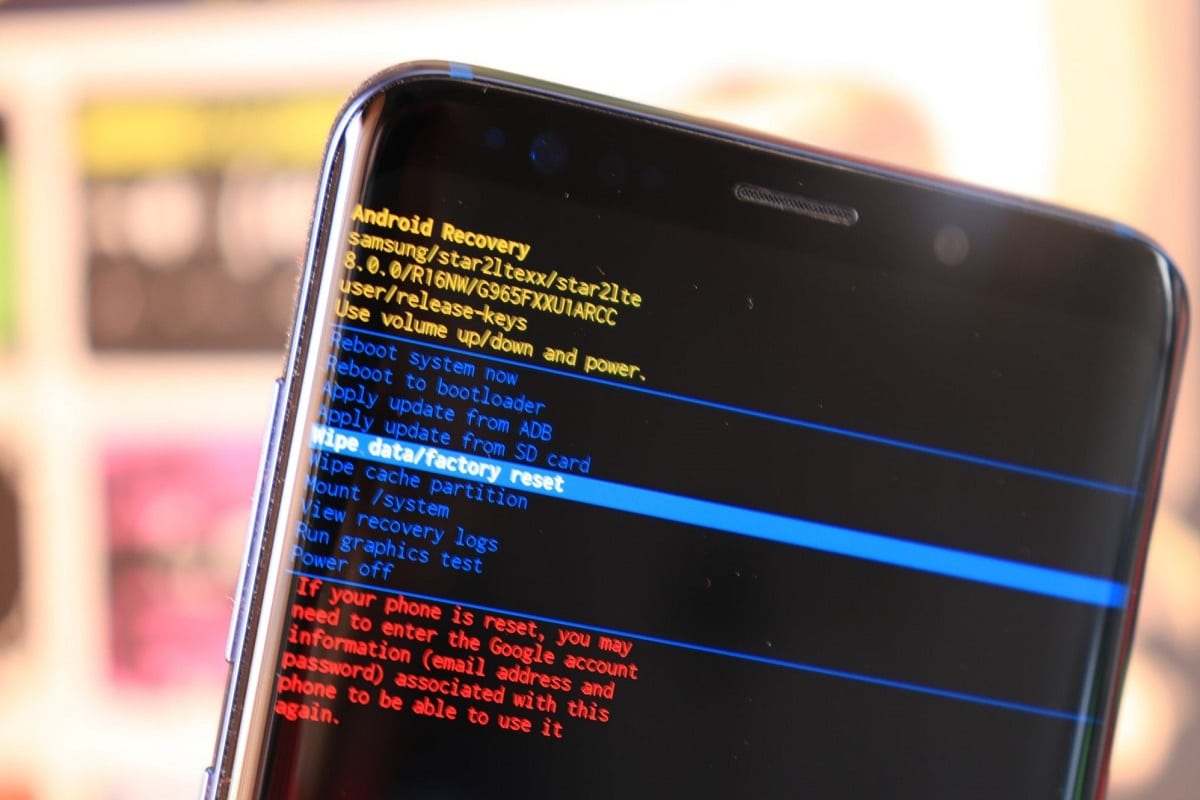
The bootloader status on mobiles can be locked or unlocked, this is usually decided and developed by the equipment manufacturer. In most cases the bootloader is locked, so it only has the ability to boot those areas that have a digital signature from the manufacturer.
Manufacturers apply this as a security measure, to make sure that the mobile can only boot the operating system that they have officially installed. Avoiding that it can be manipulated and that the codes that are loaded on the device are safe.
There are companies that usually allow their advanced users to unlock the bootloader, always leaving their warning that if they do so, it is at their own risk. Usually, Android users have the freedom to unlock it with just a key combination.
Once the Android bootloader has been unlocked, users can install third party ROMs, which are nothing more than Android alterations made by other users or unofficial programmers.
What is the advantage of having the Bootloader unlocked?
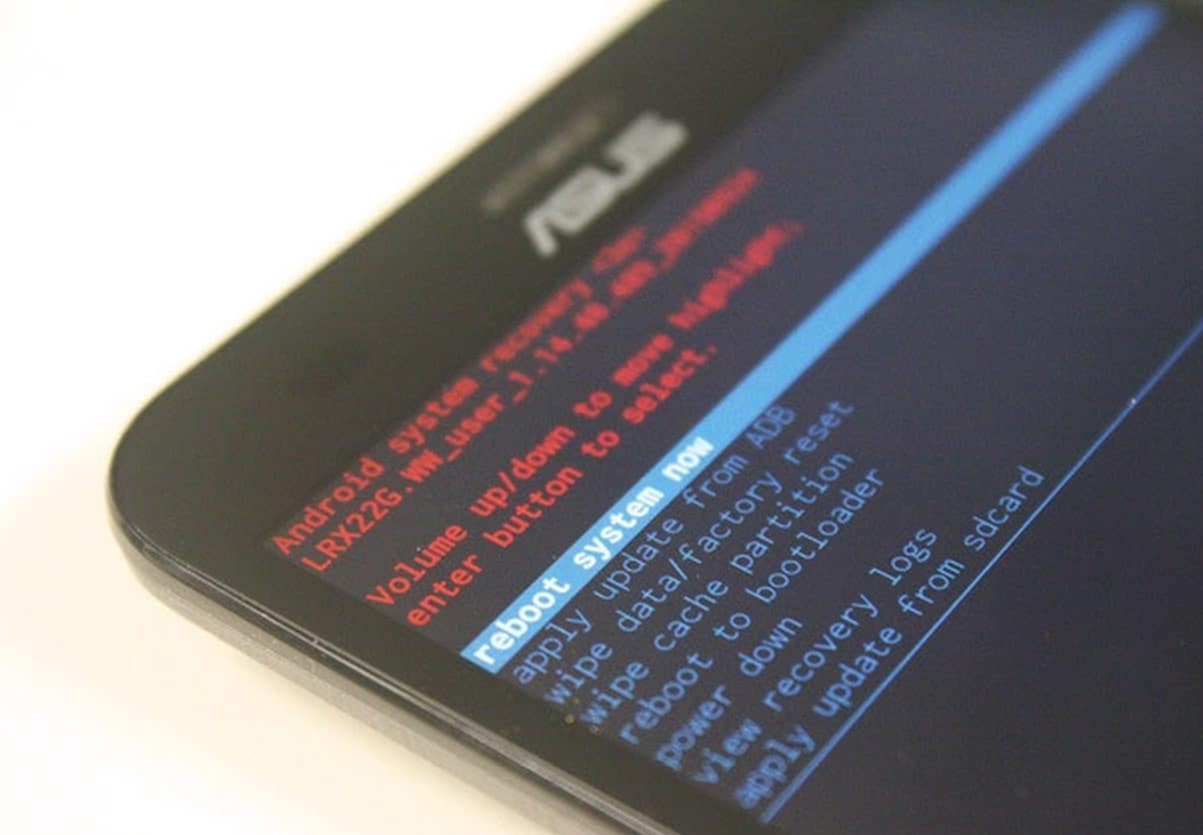
Most of the Android users prefer this operating system due to the fact that have more freedom. That is, they can go beyond the specifications that the manufacturer has created and install the modifications they want in the software.
In the case of devices with Android there is a large variety of third-party ROMs or alternative versions developed by independent programmers. With this they have achieved that mobile devices that have remained in an old version of Android and have the ability to work with a newer one.
Another thing you can do when you have the bootloader activated is to install a modified firmware, managing to have a greater customization of the device software and thus be able to change the appearance to taste.
you can even achieve modify hardware behavior, using more updated drivers or improved by third parties. However, you must bear in mind that unlocking the bootloader implies risks, since you can expose your mobile to a malware attack with which they can take important data from you.
Now that you know about bootloader, you must understand that it is a more useful option for those users who have knowledge in the area of device programming.